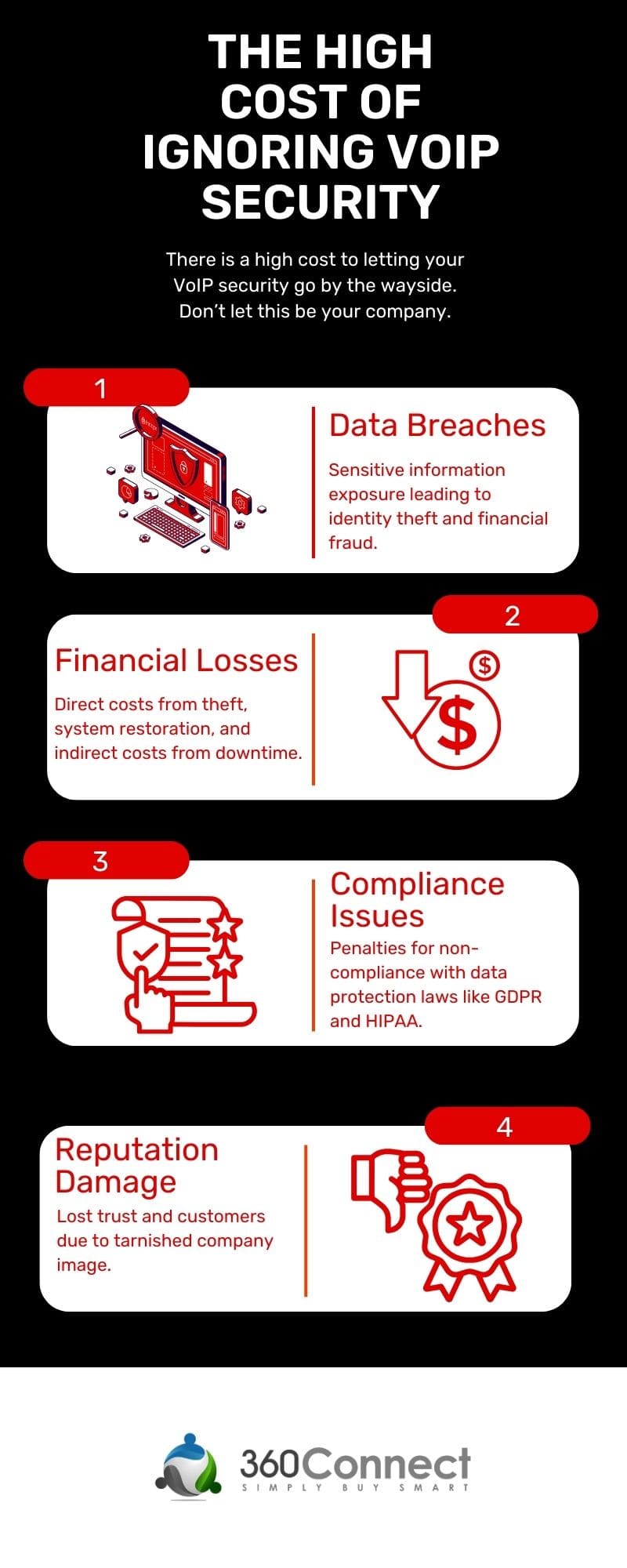
VoIP security refers to the procedures, protocols, and tactics to protect VoIP communications against unauthorized access, misuse, service disruption, and all other types of cyber threats. Because VoIP systems transport sensitive data, including voice communications, which may contain secret personal or commercial information, VoIP security is crucial. If this data is compromised, attackers can use it to commit serious privacy violations, financial fraud, and business espionage.
Types of VoIP Threats
VoIP technology has transformed communication and provides flexibility and functionality for business communications. However, its reliance on the internet and digital networks exposes it to a slew of security flaws. Here are a few of the most serious threats:
Eavesdropping:
This is the unauthorized interception of VoIP calls. Attackers may obtain sensitive information, such as personal information or company secrets, which can then be exploited maliciously or sold on the dark web.
Vishing (VoIP Phishing):
Like email phishing, vishing deceives people into disclosing private information. VoIP is frequently used by attackers to pose as trustworthy organizations and request passwords, credit card details, and other personal information from consumers.
Malware and Viruses:
Malware can infiltrate VoIP equipment and software, allowing attackers to disrupt services, steal data, or remotely manipulate networks.
Denial of Service (DoS) Attacks:
These attacks overload a VoIP network with excessive traffic, causing it to shut down and preventing legitimate communications.
Man-in-the-Middle Attacks:
Attackers may intercept and listen to communications between two VoIP users without their knowledge, potentially resulting in data breaches or fraud. They may also try to impersonate one of the callers on the line for social engineering attacks where they get employees to give sensitive information about the company or themselves.
War Dialing:
This method uses automated phone number dialing to locate vulnerable modems, fax machines, or VoIP equipment. When these endpoints are discovered, they can be used to acquire unauthorized network access.
Spam Over Internet Telephony (SPIT):
VoIP customers are targeted with bulk unsolicited calls. The goal is either to spread scams, fake information, or other malicious goals.
How to Protect Your VoIP System
There are some key moves you can make to ensure your VoIP System is protected and secure from threats. Remember, the internet and malicious attacks are always evolving, so you’ll want to stay up to date with current security trends.
Manage Default Setting and Password Safeguards:
VoIP devices and software come with factory defaults, including default passwords that are frequently well-known and easily accessible. Change these immediately to unique, strong passwords and keep them up to date.
Secure Access Controls:
Implement robust access control measures. This includes creating user accounts with access to specific features and information. This safeguards your data and keeps employees safe as well.
End-to-End Encryption:
Use VoIP providers that provide end-to-end encryption for calls and messaging. This ensures that the content of the communication is only available to the sender and the intended recipient. Your Wi-Fi network should also be encrypted with WPA2 on your network.
Transport Layer Security (TLS):
To encrypt the signaling traffic connected with VoIP calls, TLS should be utilized. This safeguards against some sorts of attacks by preventing the interception of call setup information.
Firewalls:
Install firewalls developed expressly for VoIP traffic, known as application-layer gateways (ALGs), which can inspect and filter VoIP traffic.
Virtual Private Networks (VPNs):
VPNs can provide a secure tunnel to route VoIP communications over the internet for remote users or branch offices. This is especially true when employees join from potentially unsafe external networks.
Regular Security Audits and Monitoring:
Conduct frequent security audits on your VoIP system to look for vulnerabilities. Monitor the system’s activities via monitoring tools, looking for unexpected patterns that could suggest a security concern.
5 Best Phone Plans for Businesses
Learn MoreVoIP Security Policies:
Create and implement security policies that govern how the VoIP system is to be used and how security is to be maintained. Strong password policies, update schedules, and incident response procedures should all be included.
Remote Device Management:
You need to have the ability to update/wipe/remove devices even when working remotely. This is not only important for remote workers, but also for making sure your security team can tackle any problems even when at another location. This security measure is especially important for enterprise phone services.
Firmware & Software Updates:
Manufacturers frequently issue firmware updates for VoIP equipment. These updates can address known security flaws, introduce new features, and enhance performance. VoIP applications and servers also need to be regularly patched to address security vulnerabilities.
Monitor Your Calling:
To prevent toll fraud, ensure your VoIP service blocks 1-900 numbers (unless you do work internationally). To prevent restricted/private calls from getting through, allow call blocking and send a message instructing the recipient to enable their caller ID.
User Education and Training:
Educating your team can go a long way in protecting your business. Train employees to spot and report phishing attempts. VoIP can be used for phishing (vishing), so employees must be aware of how to identify questionable calls. Also, encourage employees to report when incidents do happen as soon as possible.
Need a VoIP Provider to Help with Security?
Do you need a VoIP provider that can help with your security? Don’t worry, we’ve got you covered! Just fill out our 1–2-minute form and we’ll contact you to verify your information and needs. From there, up to 5 suppliers will reach out to you with quotes. This process is 100% free.

